
Prevent leakage of sensitive data with
minimal effort to value!

Prevent leakage of sensitive data with
minimal effort to value!
Relating to negligence
Relating to criminal insiders
Relating to user credential theft
Organizations have had little success protecting sensitive data from unauthorized access via external attacks or insider risks. This has left them exposed to consequences
What are the consequences?
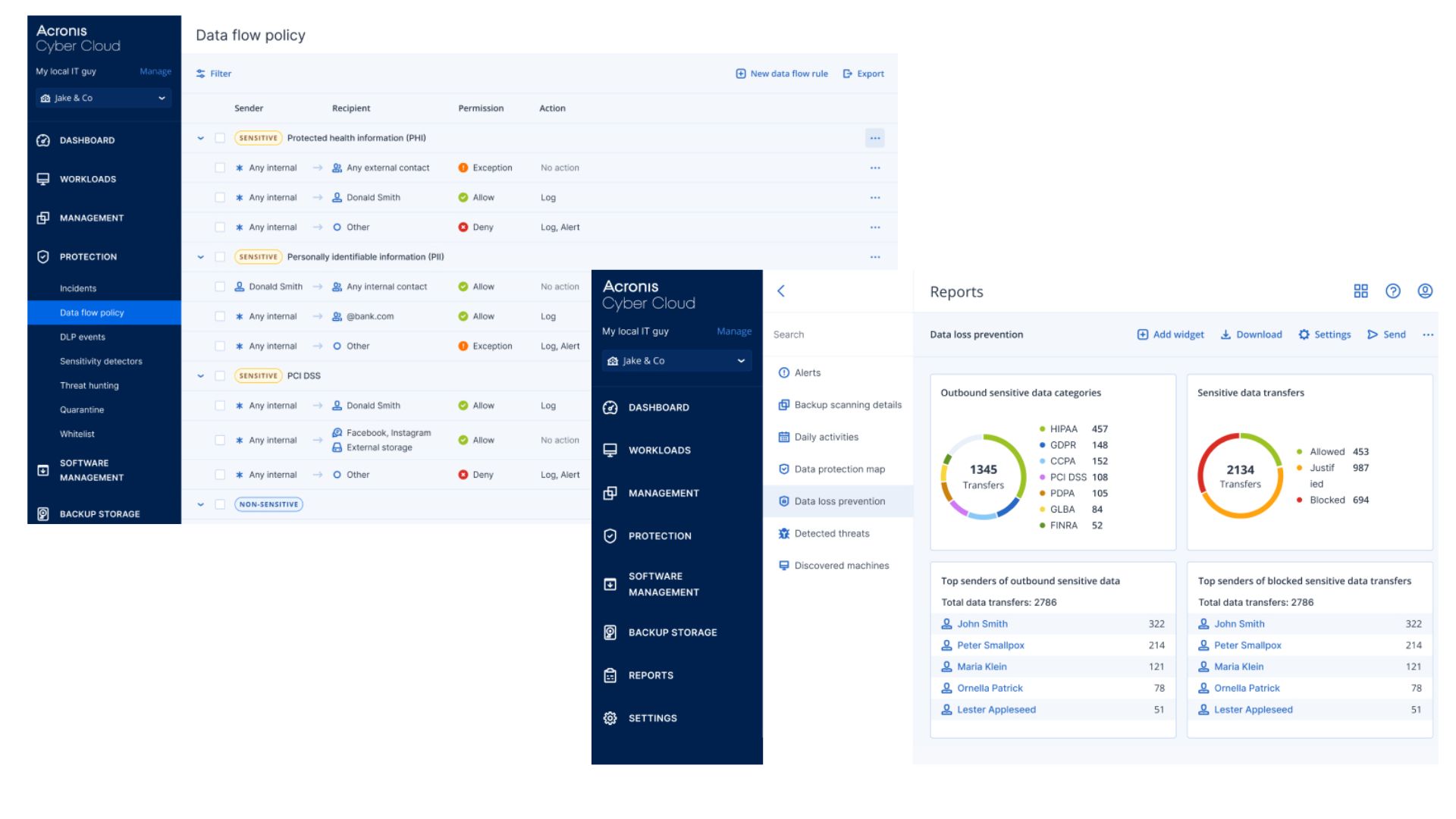
Acronis Advanced DLP empowers you with unmatched provisioning, configuration, and management simplicity, to prevent data leakage from client workloads and strengthen regulatory compliance. A unique behavior-based technology automatically creates and continuously maintains business-specific policies, without requiring months to deploy.
Ensure there’s no leakage of data through local channels by controlling which users or groups can access ports, peripheral, storage, redirected, and mobile devices. Access controls can be enforced depending on the time of day and day of the week.
Prevent data leakage via network communications of Windows endpoints with context-aware controls. Increase business process compliance by enforcing controls over both plain and SSL-encrypted traffic.
Have thorough control over transferred or accessed content with content detection based on pre-built templates of Regular Expression (RegExp) patterns and industry-specific keyword filters (HIPAA, PCI, etc.) for structured data, and data fingerprinting for unstructured data.

10
HTTP/HTTPS, FTP/FTPS, Telnet
Yes
This native integration enables Acronis DeviceLock agents to be deployed and fully managed via Group
Continuous data protection
Control all your devices from one location
Yes
Receive credentials for the centralized portal instantly seconds after your order.
Ease the resource-consuming processes of deploying and managing an enterprise DLP solution. Acronis DeviceLock DLP offers a set of central management consoles based on an organization’s IT environment, along with the ability to manage and deploy natively through Group Policy.
Prevent tampering with DLP policy settings locally on protected endpoints, even by local sysadmins. When enabled, only designated Acronis DeviceLock DLP administrators using the central management console can uninstall, upgrade the agent, or modify DLP security policies.
Extract and inspect textual data from more than 30 graphical formats, including graphical files, screenshots, pictures in documents, emails, and instant messages. Improve DLP cybersecurity on endpoints both inside and outside the corporate network.
Prevent unauthorized data transfers at their earliest stage – between application and documents – through the Windows clipboard and print-screen mechanism. Block specific operations, such as print-screen, or granularly control them based on copied content.
Prevent tampering with DLP policy settings locally on protected endpoints, even by local sysadmins. When enabled, only designated Acronis DeviceLock DLP administrators using the central management console can uninstall, upgrade the agent, or modify DLP security policies.
Gain visibility over data flows, data protection, and user activities related to them with powerful built-in compliance-related reports based on audit and shadow logs, permissions and settings, connected plug-and-play devices, and user activities.
Automatically collect audit and shadow logs and deliver them to the secure central repository to ease security investigations and auditing, thanks to Acronis DeviceLock DLP agents. Traffic shaping and data compression for log delivery and load-balancing help reduce network impact.
Shorten reaction times with real-time SMTP, SNMP, and SYSLOG alerts based on unauthorized actions delivered directly to SIEM systems and administrators.

